Christopher Woodley
Software Engineering ePortfolio
Professional Self-Assessment
My path through the Computer Science program began in January 2018. My passion for computer programming drove me to fill in the gaps in my previous knowledge and helped to strengthen my skills all the more. My passion for computer programming began several years ago, using languages such as Basic, Pascal, and C++ to build simple programs to test out how things worked. Since then, I’ve utilized my skills in programming to help locate solutions for work related issues through the means of software development, generating applications to be used to help streamline processes and build permanent solutions that are utilized to this day in my company. The path to my degree has been stemmed mainly due to my wish to truly devote myself to software development, taking on challenges found with nothing more than the problem and requirements, and help to develop solutions that can help resolve more issues.
My time in the Computer Science program has aided me in expanding my knowledge in various skillsets, from learning new programming languages, to developing better critical thinking skills and putting new methodologies of development at my disposal. In the short time I have been in the Computer Science program, I have spent my time increasing my knowledge not only of new programming languages, such as Java and Python, as well as new skillsets, such as building SQL and NoSQL databases, but also utilizing all these skills as a whole to develop complete projects, finding solutions and being better prepared to face each incoming challenge with the same mindset and purpose.
Collaborating in a Team Environment
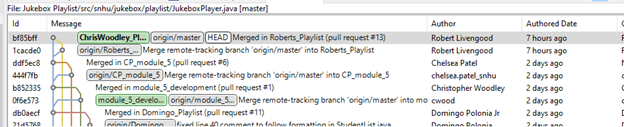
Throughout this program, the knowledge that development is more than just one person coding has helped in identifying means of working better within a team environment. Utilization of code hosting platforms, such as GitHub, has aided team work by having a single place where all work can be stored, allowing for review of the changes being made, identifying conflicts, and working through with the team to determine the best course of action. Below is an example showing not only the handling of branches within a team repository , but also showing a review of code, adding in detail to better explain what has been located and any changes that would need to be made.
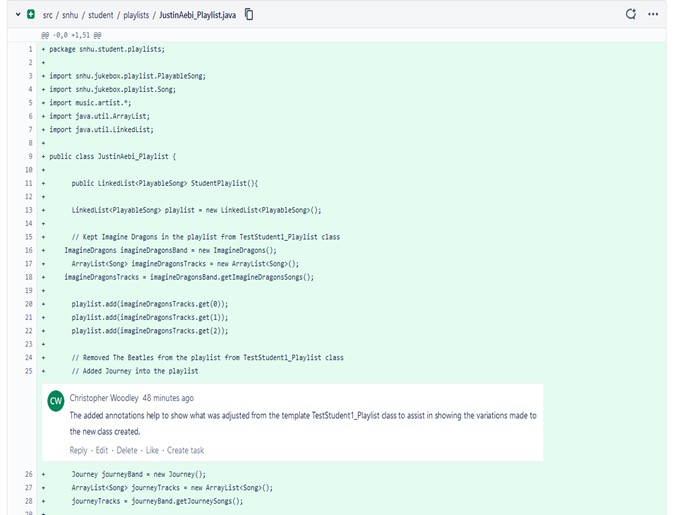
In addition to this, utilization of comments and proper naming schemes is helpful in assisting those having to modify and upgrade the source code by not only outlining the main objective of a given set of code, but to do so on a line-by-line basis, explaining the intention and expected results. In so doing, the source code is much easier to not only understand, but to traverse, and identify where adjustments and updates will be needed.
During my tenure in the Computer Science program, I was able to employ strategies for building collaborative environments that enable diverse audiences to support organizational decision making in the field of computer science by utilizing these very tools. With GitHub, I was able to ensure that my work was properly aligned in individual branches (Example 1) and was properly reviewed by others prior to pushing into the main branch to ensure that the code was not only properly vetted (Example 2), but also that there were no conflicts within it. This was helped by means of proper comments and naming schemes to ensure that the source code was simple to follow for those reviewing, making for a more streamlined approach.
Communicating to Stakeholders
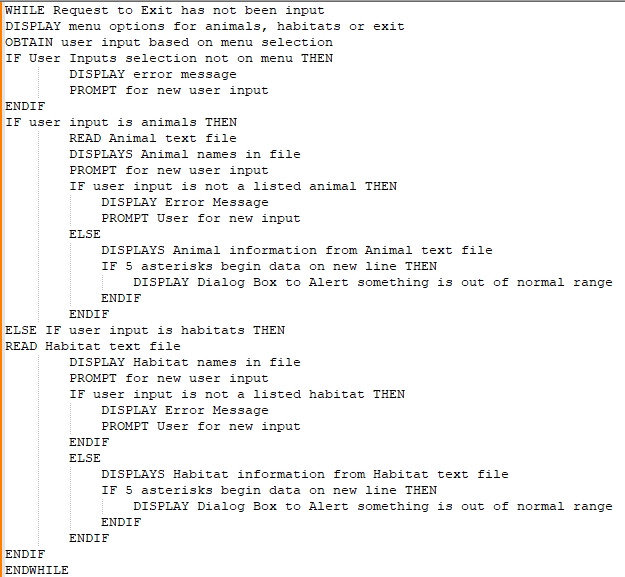
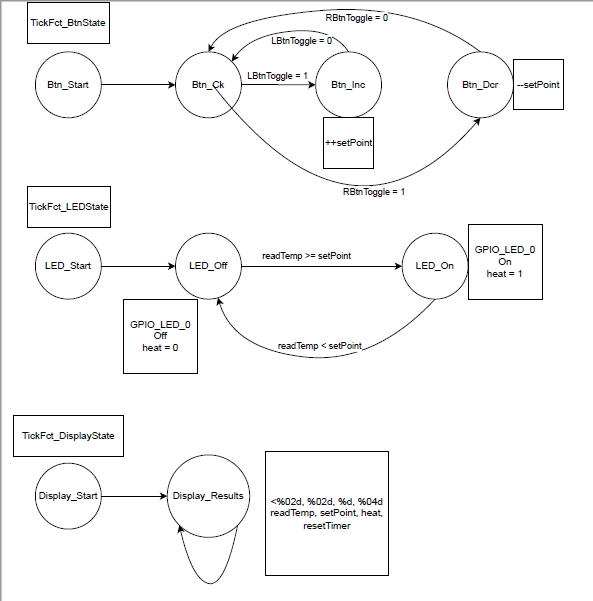
Not only having to ensure that your team is kept apprised of your work, the stakeholders, be them an outside client to a group of internal customers, their understanding and feedback to the progress on a project is vital to ensure not only the end results are met, but they are met to fit all the needs outlined within requirements. First and foremost, communication must be done at the outset, to first gather their vision of the end result, and from there be able to obtain the necessary requirements to even begin the development. From these, the next logical steps would be development of outlines and tools in which to better comprehend and map out the application, such as pseudocode or a workflow. It is from these basic parts that begin the documentation process, better to flesh out and give more depth to the skeleton built with the initial steps. With a mutual approach between all parties on how the project will develop, this not only allows the team to better understand the end result, including those who will develop as well as test, but allows the stakeholders to better know what the end result will be for their own means, allowing them to better approach their own acceptance testing.
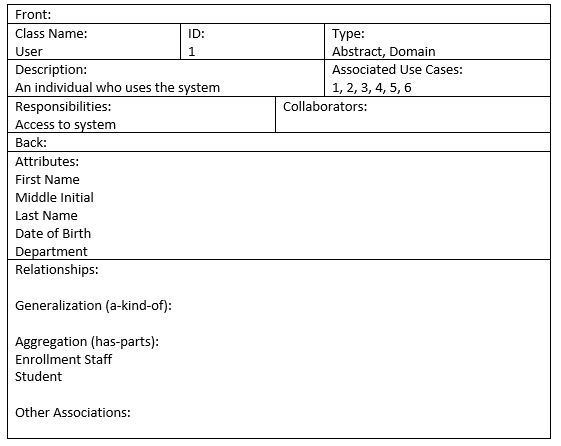
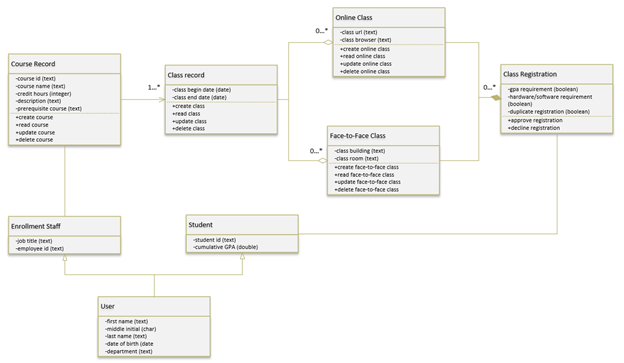
During my time in the Computer Science program, I was able to design, develop, and deliver professional-quality oral, written, and visual communications that are coherent, technically sound, and appropriately adapted to specific audiences and contexts. This was done by using a combination of all the above referenced methodologies, from developing simple pseudocode to better outline the basic flow of the program (Example 3), which in turn could be turned into proper workflow charts to help determine how each individual step will work (Example 4), including how possible variations may branch out from a one task to another. Additionally, by use of object-oriented design, I could easily map out individual classes into use cases (Example 5), which can be properly viewed within a sequence diagram (Example 6). With these tools, the ability to share the plans and status of the project with all stakeholders in the project, ensuring that all known information was shared with the team as a whole.
Data Structures and Algorithms
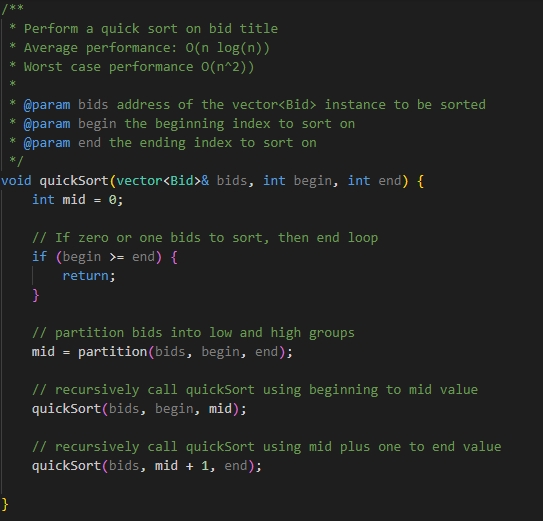
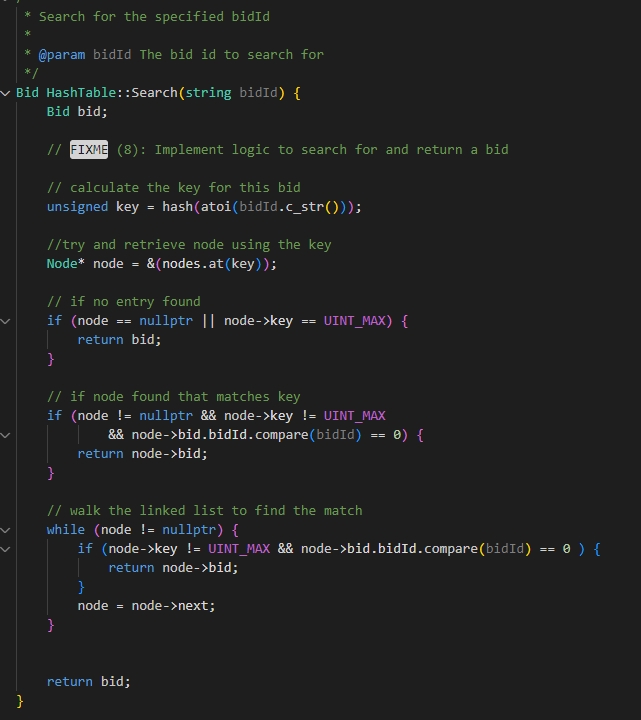
In any manner of development, one is only able to build solutions based on a solid structure, and from there the application can be properly fleshed out as long as it can be built upon said structure. By building up in a modular fashion, not only does this allow for simpler development and testing by ensuring things are built piece by piece, but also allows for ease of usage not just in multiple instances of an application, but in multiple applications as it can be plugged in as seen fit. Usage of variations of data types and structures, such as structs in C/C++ and classes in Java allow for multiple data elements to be accessible without needing to build more complicated programs. Lastly, the use of algorithms helps to find means of traversing data in a more organized and simpler manner, leading to reducing computing time for execution, leading to quicker results for the end user.
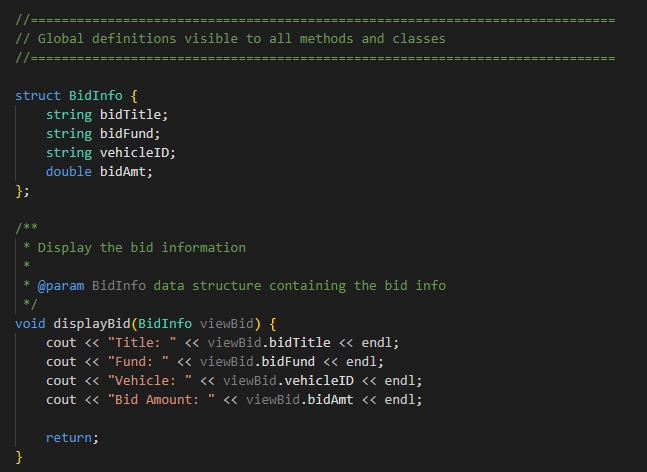
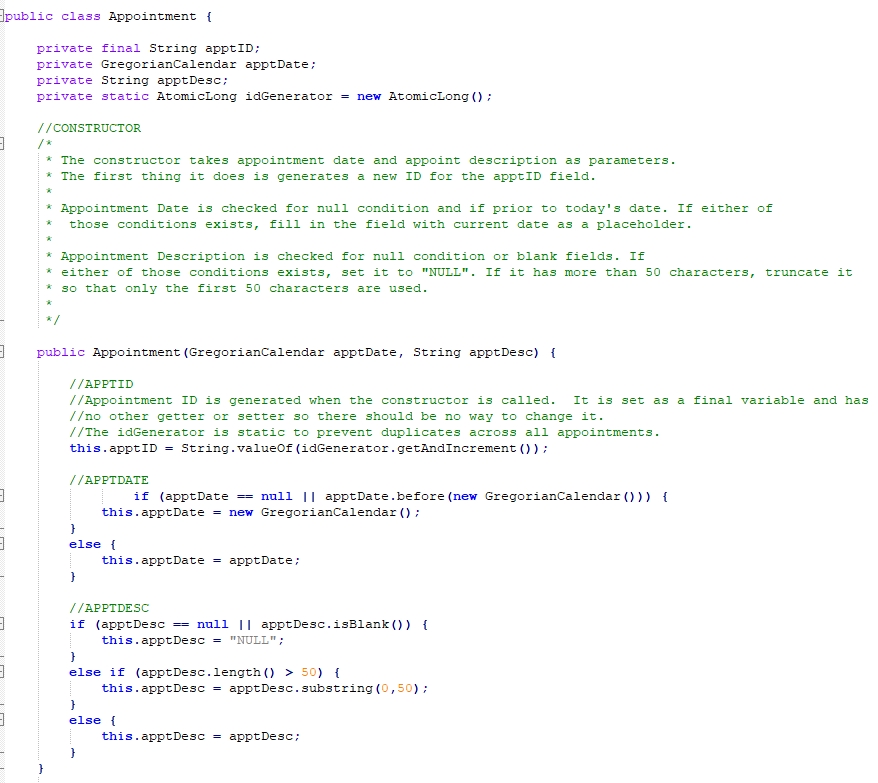
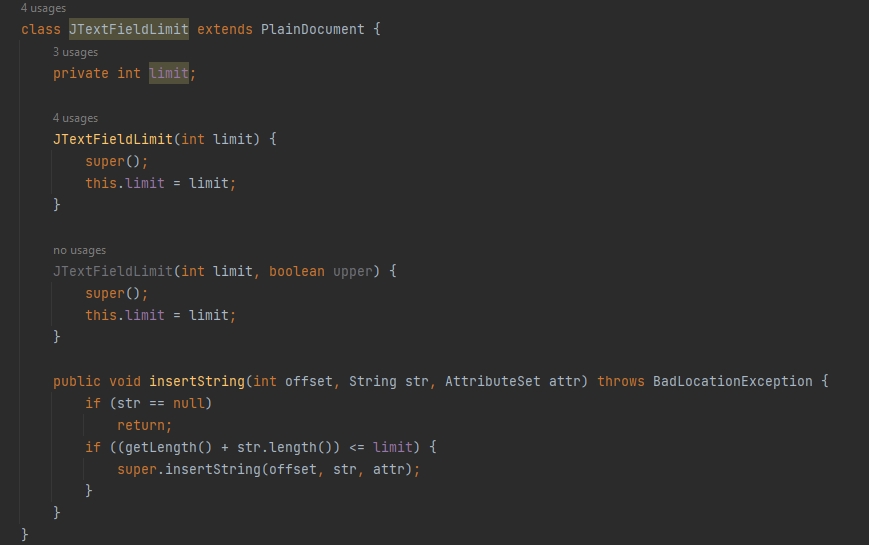
Using these methods, I was able to design and evaluate computing solutions that solve a given problem using algorithmic principles and computer science practices and standards appropriate to its solution, while managing the trade-offs involved in design choices. This was done via a modular approach, by building up individual structures (Example 7) and classes (Example 8) that could better be used for the purpose of a singular task, such as creating an object to be created, edited, and removed as needed. The building of algorithms, such as vector sorting (Example 9) and hash tables (Example 10), helped to build up the data structures into proper formats for ease of adding, removing and seeking data as needed for the execution of the application. These methods combined not only ensure a solution that can meet all requirements, but also ensures no trade-off in the design choice by ensuring that efficiency is ever a forefront thought.
Software Engineering and Databases
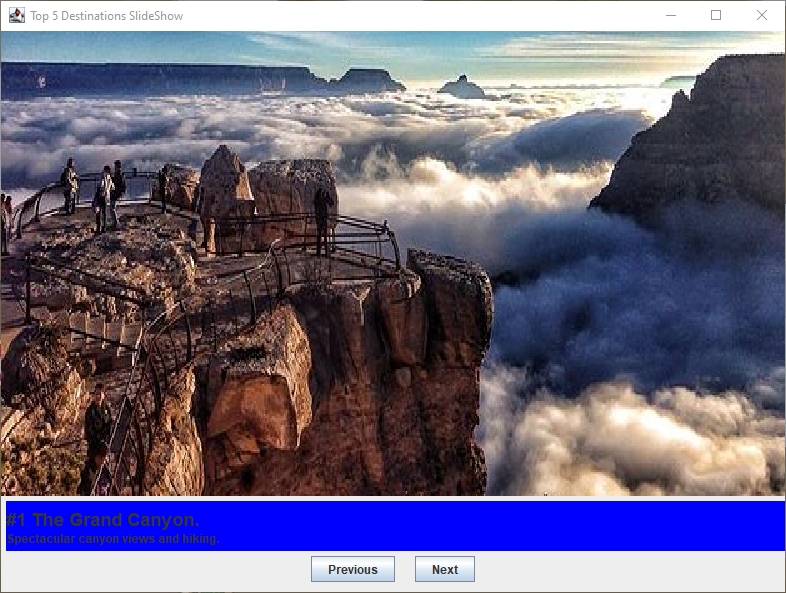
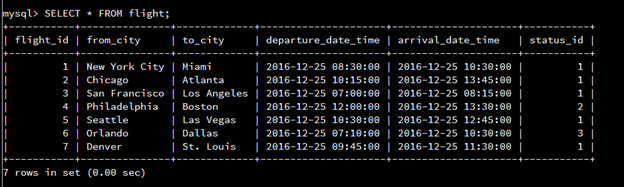
In any means of development, a developer can only be as good as the tools they have at their disposal to reach their solution. In software development, this remains true in that without particular tools that can be utilized, a program can only do so much. With tools that help to better visualize solutions and the application as a whole, such as graphical user interfaces, to how data can be properly stored not just for use during program execution, but for long term storage as well, such as databases and file storage, the use of these tools help to add depth to any development project, allowing for more functionality for the end user for more prolonged and ease of use.
In these ways, I have demonstrated an ability to use well-founded and innovative techniques, skills, and tools in computing practices for the purpose of implementing computer solutions that deliver value and accomplish industry-specific goals. By being able to create a graphical user interface that is more intuitive to the end user (Example 11), thereby allowing them an easier front end to be able to access and utilize the application leads to allowing a wider audience to be able to make use of it. Adding in databases such as SQL (Example 12) and NoSQL (Example 13) database, as well as utilizing pulling and storing data in text-based files helps to allow data to be stored properly, ensuring user data is permanently accessible for as long as the user has need of it, helps to push for a more long-term solution.
Security
Along with reaching the desired solution, the ability to keep said application both stable and secure holds a great deal of merit. When considering the stability of an application, it cannot be easily broken or manipulated to do beyond its desired scope. In terms of security, the fear of personal data being accessible to anyone will always be a concern that need to be approached with the utmost care. By adopting a DevSecOps methodology of software development, keeping security as much a part of the development process as any other aspect ensures that security is never just an afterthought, but a main aspect of the process.
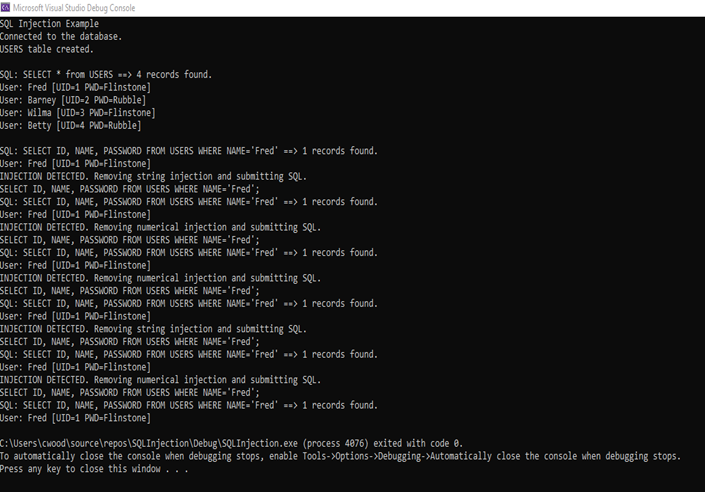
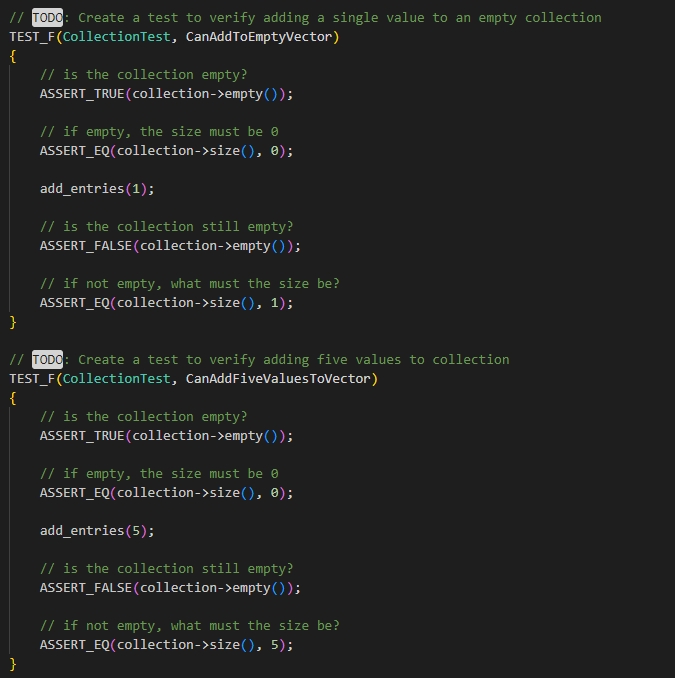
It is in these ways that I have developed a security mindset that anticipates adversarial exploits in software architecture and designs to expose potential vulnerabilities, mitigate design flaws, and ensure privacy and enhanced security of data and resources. By considering that security needs be considered during the development process, taking measure of the requirements helps to determine possible vulnerabilities. Such in the case of allowing user input to be made, issues such as SQL injection (Example 14) and buffer overflow could be a concern. However, by ensuring the data input is properly validated and only allowed to the extent as per requirements (Example 15), this helps reduce these types of issues. Even at times there can be unforeseen circumstances, but the code must go on and the application must not break. By adding in exception catches and error handling, these unforeseen issues, be them due to outside interference or an error yet to be discovered, the error will be captured and handled by letting the user know, but still will not cause the application to break, which in turn ensures that it runs as needed, but also secures the source code from those who should not have this access. Lastly, the best method of not just ensuring that code functions as required, but that limits and validations are placed is via testing (Example 16). By building tests for the code, you can seek out the limitations, finding when things will not just pass when intended, but fail when they should as well, better ensuring that all expectations are met not just logically as per the code, but by example and execution as well (Example 17).
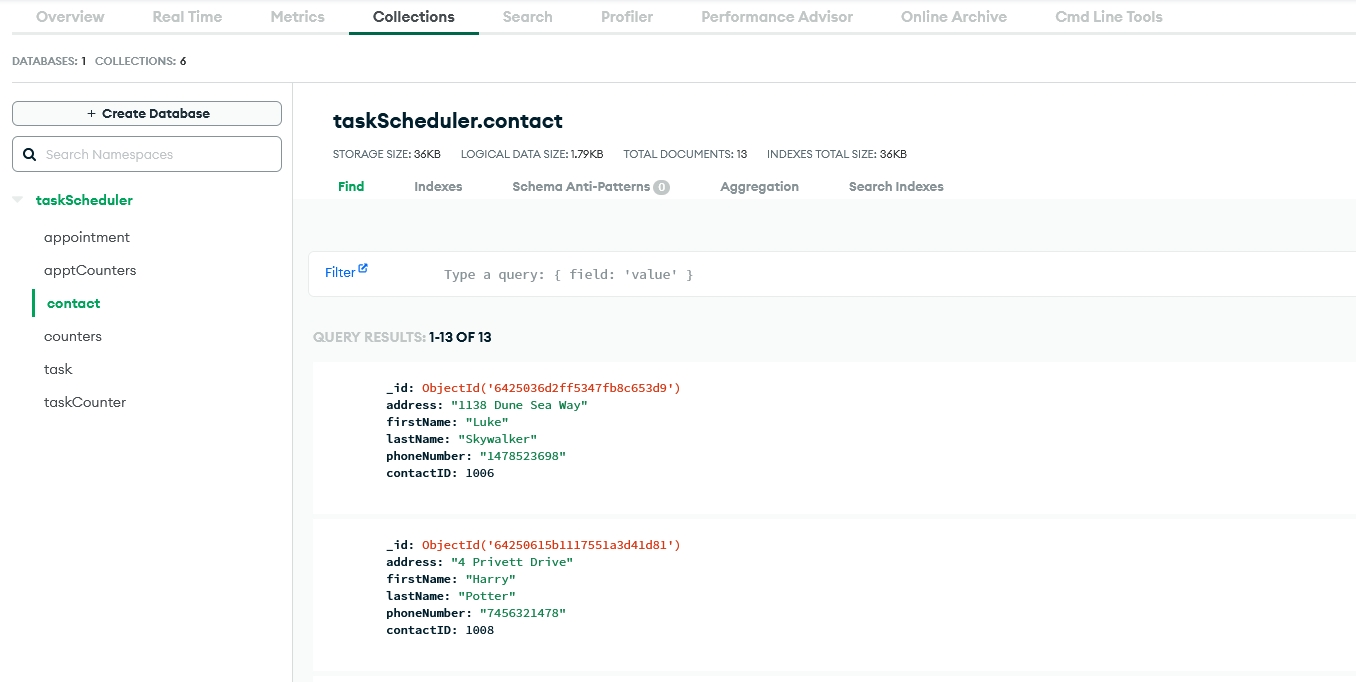
Portfolio Artifact 1 - Task Scheduler
The first artifact added to this portfolio is a Task Scheduler, which holds Contact, Appointment and Task information. The application was written in Java, and during consideration for enhancement, it was determined to keep the programming language used the same for this artifact. The reason for the selection to the ePortfolio is that the application was originally used for testing purposes only, without any true application base developed. With the basic structure already built, it was a perfect example to not only complete to make it functional, but to make the enhancements to make it function in a more user-friendly manner. By adding a graphical user interface generated by Java forms, this helps to expand the audience of the application wider as the user-friendly design will make it more appealing to more. By taking the already existing data structures created for the contact, appointment, and task elements, and putting into use the CRUD functionality, this will help show the ability to reuse assets for expanded functionality. Lastly, by implementing a MongoDB database that will hold the data, this helps to increases the usability of the application, allowing for long term storage of information, but also to allow for easier access to the existing data elements via the MongoDB query functionality to insert, read, edit, and delete user information.
Portfolio Artifact 2 - Monitoring System
The second artifact selected is a Monitoring System written in Java. The original application was built solely to pull data from a text-based file and display the information to the terminal. The reason for inclusion of this application is that the structure of the application was perfect for an upgrade due to the limited functionality that was considered. First off it requires outside data to function, which was original a text-based file. The update was made to utilize a CSV file which does not alter its text-based functionality but allows for easier reading and writing to the files due to the delimiter. With data being read from the text file, the next step was to ensure that alterations to the data could be made, such as adding additional records, or even updating existing information, to allow more versatility to its purpose. Additionally, the addition of utilizing an algorithm, in this case a binary search tree, made the most sense to cut down on search times through large volumes of data, to have better return time. Taking steps further, the use of the algorithm which for most would be helpful using it with number-based values (such as a system generated unique identifier), taking the steps to push the algorithm to build up based on strings helps to better show an understanding at the versatility that these algorithms can have with the data elements utilized, making it so even text-based data can be used for ease of searching.
Further details regarding the enhancement of the selected artifacts can be found in the artifact sections below.
| Home | Code Review |
| Artifact 1 - Task Scheduler | Artifact 2 - Monitoring System |