Christopher Woodley
Software Engineering ePortfolio
Artifact 2 - Monitoring System
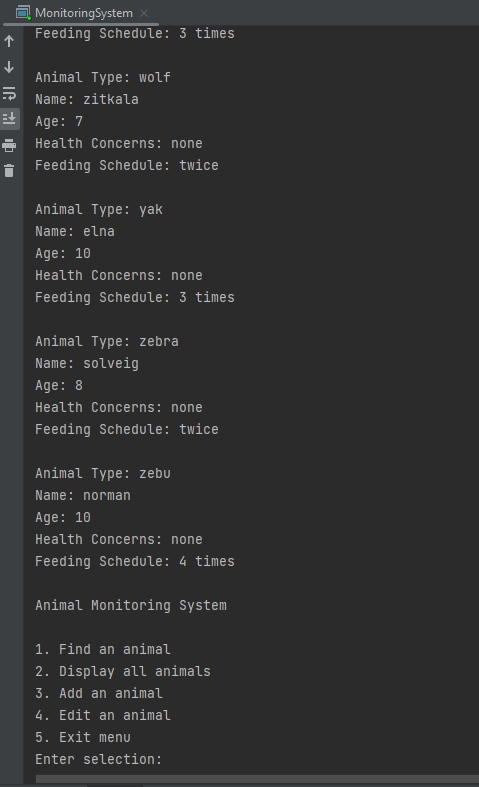
Description
The second artifact I have selected is a Monitoring System. The original application was developed in January 2021 for use in IT-145 - Foundation in App Development for the use in showing the ability to read data from a separate file and output in the application. The application will prompt user to select either Animal or Habitat monitoring, in which the file in question will be pulled and allow users to search and display the information found in the file for the requested record.
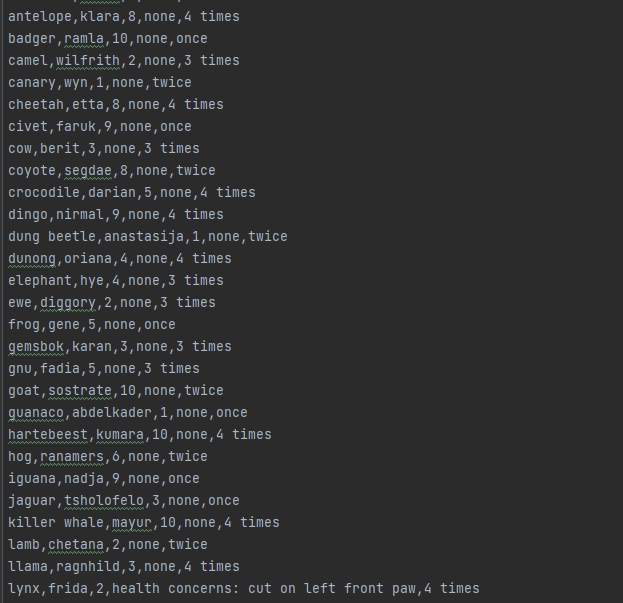
Inclusion
When selecting artifacts for the use in the ePortfolio, this application was an easy selection to help outline the usage of algorithms in use of making searching and displaying information take less execution time as the larger the data to be sorted, the better it will reflect the usage of the algorithm. Seeing how the original application used basic text based files with limited data, for this to show the true merit of the algorithm was to expand on the data, by using CSV text based filed instead, which keep the data aligned in separate sections while not making the file harder to recreate and traverse. While the original application was just for reading off the file, this needed to be adjusted, allowing for data to be not just read, but new items added and updates allowed for existing data. The ability to take large data and not just make it accessible, but to make the execution of data manipulation not cause a large delay for the end user made this a perfect fit for inclusion.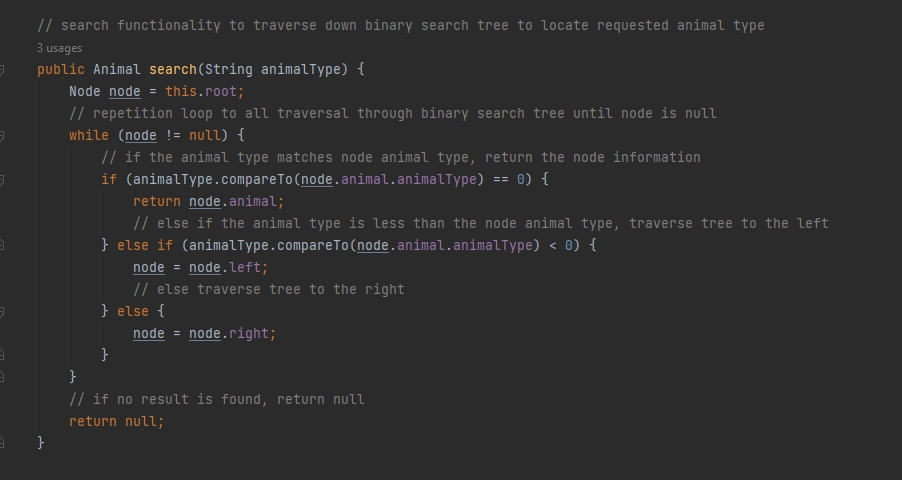
Skills and Abilities in Software Development
Employed strategies for building collaborative environments that enable diverse audiences to support organizational decision making in the field of computer science:- Built and implemented basic template of monitor system for ease of adding additional options that utilize the same functionality of existing systems
- Source code commented both with overall functional information but also line by line detail on what section of code is executing what function
- Implemented binary search tree algorithm to monitoring system to pull incoming data into individual nodes, allowing for easier traversal for finding and updating data elements
- Altered binary search tree to utilize searching for string based data versus numeric data to remove need of unique numeric identifier for use in search nodes
- Implemented two separate binary search trees to fit in with specific files needs, thereby creating a template based code for adding additional systems with the same binary search tree functionality when adding new systems to monitor
- Added error handling and catches to ensure application will prompt user if error but will continue execution, ensuring no error can open backend data due to execution breaks
- Ensured catches to invalid data selections were added to each input section, ensuring anything beyond acceptable data will result in error and will not cause intrusion
- Added checks for file closure after completion of file usage to ensure data is opened only for pulling required data and closed once completed
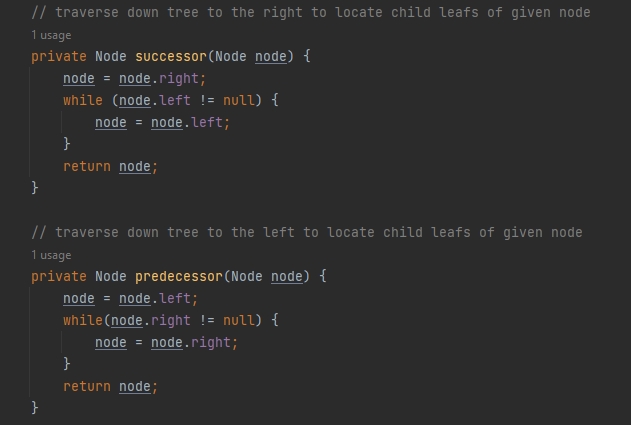
Reflection
The process of enhancing this artifact has helped to put new perspective in terms of how to utilize my skill set when making updates and enhancements to programs. With this artifact, the main concern was the limited functionality that was originally developed, since it was utilizing a very small data set and also only allowing the user to view results, not make any alterations. By pushing for CSV text based file, I was able to keep the data aligned together without needing to expand the list into something that would be first harder to generate and also more complicated for manual review. With the expanded data, the need for a better method of pulling data was needed, since execution time for each function should be quick for a responsive application. The binary search tree was the easy selection here given it helps to implement a "divide and conquer" aspect for the data, allowing the system to view the required field and sift through the nodes by comparing and then moving to the respective branch depending on those results, offering less computing time for searches. However, since most binary search trees I have developed used numeric based parameters which would require additional fields if added to the current application. Due to the data not including any unique numeric code, this method was enhanced to take in a string parameter for use in the functionality, which required some alteration to ensure that string data was acceptable via the binary search tree.
The main challenge in this enhancement was the implementation of the binary search tree. At first, the implementation was to utilize a sole binary search tree class for both files being utilized. However, the issues found during this implementation was that due to differences in file structure and data elements, it wasn't feasible to continue with how the trees needed to be, which was causing errors in the traversal and data not being located properly. So instead one complete binary search tree was implemented and tested on the Animal file and worked on all executions, and then was taken as template for the Habitat binary search tree, with little adjustments to be made to ensure it worked similarly, and during testing was found to work without issues as well, thereby taking code and reusing it as best as possible. This helped solidify the practice of reusable code, which may not always be a class that can be called by several other functions but merely a set of code that can plugged in and adjusted as needed, making it a standard for uniform source code.
After completing the enhancement, I found that the current application gives a more valid picture of my current skill set in software development. Taking the structure that was made available already had the basic set up required, however even this required adjustments. First was to consider how best to protect the application as well as ensure that unforeseen errors would be better handled. Adopting the DevSecOps methodology helped when reviewing the code to find areas with possible issues, such as not closing out files after use and not validating input from users, to ensure that proper checks were always put into place and the right catches were added to ensure the application will not cause an unexpected crashes. Additionally, the issue with the binary search tree needing to be put into each section was a good measure of adaptability, ensuring that regardless of the issues experienced during development, the end goal was kept in the forefront, and any adjustments needing to be made were done with the end product in mind. These methods of resolving issues helps in not just showing that adaptability is vital in the development process, but can be put into use in other aspects of the DevSecOps process, ensuring that regardless of issues and obstacles, my ability to adapt and proceed will not cause a delay in the development process.
| Original Code | Enhanced Code |
| Home | Self-Assessment |
| Code Review | Artifact 1 - Task Scheduler |